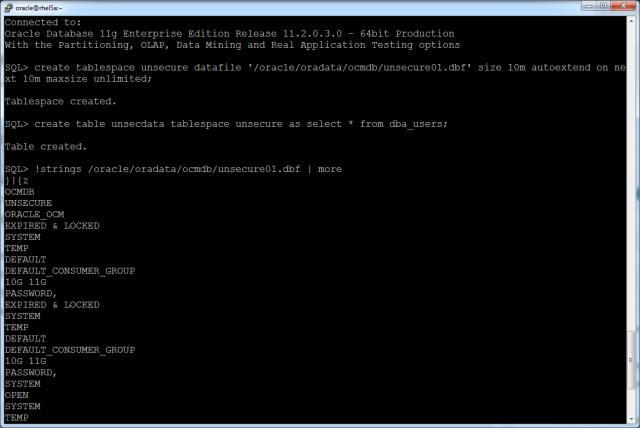
Now that I have a freshly-installed Oracle Solaris 11 server, I need to be able to remotely run and access installation media/menus that have graphical elements (GUI). One of the best ways to do this is via a VNC connection, where the installers will run on the server itself, and only the output is sent to the client/remote PC over the network, as this will mitigate latency issues that could be faced if running the installer itself remotely.
In Oracle Solaris 11, as the default out-of-the-box installation is a text-based installation with minimal packages configured (unless you opt for a virtual machine image-based installation), this means that the required packages will need to be installed and configured first, before running the VNCserver on your Oracle Solaris server.
If you were to try starting a VNC server, this is what you would expect to see currently:
root@sc2:~# vncserver :1
-bash: vncserver: command not found
To start off, first we will need to connect the Oracle Solaris server to the internet, in order to access Oracle’s package repository (the default repository that comes pre-configured during the installation of the operating system). Of course, you could also use a custom repository hosted on a machine within your local network, but in this case I will be accessing Oracle’s package servers directly.
So, lets have a look at the current state of my internet connection, by doing a few simple tests, while connected as the root user
NOTE: Several significant changes in the way the networking (consisting of the hardware, device, network later and interface layers) works in Oracle Solaris 11 might be worth looking through first, before messing about in-depth with your network settings.
Let’s have a look at the datalink layer, using the dladm and ipadm commands..
root@sc2:~# dladm show-link
LINK CLASS MTU STATE OVER
net1 phys 1500 unknown —
net0 phys 1500 up —
Current datalinks that are active, net0 and net1 for my two interfaces (or are they?)
root@sc2:~# dladm show-phys
LINK MEDIA STATE SPEED DUPLEX DEVICE
net1 Ethernet unknown 0 unknown e1000g1
net0 Ethernet up 1000 full e1000g0
The ‘show-phys’ option shows me a bit more detail, and does confirm that the datalinks belong to two separate devices, the network interfaces e1000g0 and e1000g1 respectively. But as can be seen, the net1 link belonging to the device e1000g1 is currently in an unknown state, as it has not been configured during my installation. Let’s first fix this (though in truth it is not strictly necessary for setting up VNCserver, and is more for completeness).
root@sc2:~# ipadm show-if
IFNAME CLASS STATE ACTIVE OVER
lo0 loopback ok yes —
net0 ip ok yes —
Here I can see what appears to be only the first network device and the loopback adapter currently being assigned IP addresses on my server.
root@sc2:~# ipadm show-addr
ADDROBJ TYPE STATE ADDR
lo0/v4 static ok 127.0.0.1/8
net0/v4 static ok 192.168.0.66/24
lo0/v6 static ok ::1/128
net0/v6 addrconf ok fe80::250:56ff:feb4:26/10
This output confirms it, there is currently no IP address assigned to my second network device, the e1000g0 physical device that is utilizing the net1 datalink.
At this point, first I’d like to add the IP address found in my hosts file for the private interconnect (marked as sc1-priv and sc2-priv respectively in my /etc/hosts file) before proceeding further.
root@sc2:~# ipadm create-ip net1
root@sc2:~# ipadm show-if
IFNAME CLASS STATE ACTIVE OVER
lo0 loopback ok yes —
net0 ip ok yes —
net1 ip down no —
Now I will assign an IP address to the net1 interface, create an address object for this IP address, and activate it. Once this is done, a conventional ifconfig command will allow me to ping this IP address, and the name resolution via my /etc/hosts file should also work.
root@sc2:~# ipadm create-addr -T static -a local=10.10.10.66/24 net1/v4static
root@sc2:~# ipadm up-addr net1/v4static
root@sc2:~# ifconfig net1 net1: flags=1000843<UP,BROADCAST,RUNNING,MULTICAST,IPv4> mtu 1500 index 3 inet 10.10.10.66 netmask ffffff00 broadcast 10.10.10.255 ether 0:50:56:b4:0:27
Now, moving on, I need to connect to the Oracle Solaris repository, and download the necessary files for the VNCserver.
First, let’s run a few simple commands to check on the name resolution and IP addresses:
root@sc2:~# more /etc/resolv.conf
# Copyright (c) 2012, Oracle and/or its affiliates. All rights reserved. # #
# _AUTOGENERATED_FROM_SMF_V1_
# WARNING: THIS FILE GENERATED FROM SMF DATA.
# DO NOT EDIT THIS FILE. EDITS WILL BE LOST.
# See resolv.conf(4) for details.
search WirelessAP
nameserver 192.168.0.1
nameserver 192.168.0.20
root@sc2:~# more /etc/hosts
# Copyright 2009 Sun Microsystems, Inc. All rights reserved.
# Use is subject to license terms.
# Internet host table
::1 sc2 localhost
127.0.0.1 sc2 localhost loghost
192.168.0.66 sc2
192.168.0.65 sc1
10.10.10.65 sc1-priv
10.10.10.66 sc2-priv
I have a DNS server running on a Windows Server 2008 machine, and I’ve created an entry in both the forward and reverse lookup zones for this Oracle Solaris 11 machine on it (not shown here). Now I just need to ensure that I am able to connect to the correct domain and perform a few simple lookups for the IP addresses in my /etc/hosts files.
Let me first configure the correct DNS settings on for the DNS client service (the DNS server is located at IP 192.168.0.20, and the domain is MYDOMAIN.LOCAL, edit this as required):
root@sc2:~# svcs | grep -i dns online Feb_09 svc:/network/dns/client:default
root@sc2:~# svccfg -s network/dns/client
svc:/network/dns/client> setprop config/search = astring: (“mydomain.local”) svc:/network/dns/client> setprop config/nameserver = net_address: (192.168.0.20) svc:/network/dns/client> select network/dns/client:default svc:/network/dns/client:default> refresh svc:/network/dns/client:default> quit
Check the values of the /etc/resolv.conf file to ensure that the changes above have been applied:
root@sc2:~# more /etc/resolv.conf
# # Copyright (c) 2012, Oracle and/or its affiliates. All rights reserved. #
# # _AUTOGENERATED_FROM_SMF_V1_ # # WARNING: THIS FILE GENERATED FROM SMF DATA. # DO NOT EDIT THIS FILE. EDITS WILL BE LOST.
# See resolv.conf(4) for details.
search mydomain.local
nameserver 192.168.0.20
Next check and configure the default routing tables on my Oracle Solaris server and ensure that it is able to connect to the internet:
root@sc2:~# netstat -rn
Routing Table:IPv4
Destination Gateway Flags Ref Use Interface
127.0.0.1 127.0.0.1 UH 2 306 lo0
192.168.0.0 192.168.0.66 U 6 2977 net0
10.10.10.0 10.10.10.66 U 2 0 net1
Routing Table: IPv6
Destination/Mask Gateway Flags Ref Use If
::1 ::1 UH 2 30 lo0
fe80::/10 fe80::250:56ff:feb4:22 U 2 0 net0
root@sc2:~# route -p add default 192.168.0.1
add net default: gateway 192.168.0.1
add persistent net default: gateway 192.168.0.1
root@sc12:~# ping google.com
google.com is alive
After all the preliminary work has been done, now I can connect to Oracle’s Solaris 11 repository and install the solaris-desktop package (and any associated dependencies) in order to start my VNCserver:
root@sc2:~# pkg publisher -P
PUBLISHER TYPE STATUS URI
solaris origin online http://pkg.oracle.com/solaris/release/
root@sc1:/# pkg install solaris-desktop
Creating Plan –
Packages to install: 358
Create boot environment: No
Create backup boot environment: Yes
Services to change: 13
DOWNLOAD PKGS FILES XFER (MB) Completed 358/358 52154/52154 534.6/534.6
PHASE ACTIONS
Install Phase 84080/84080
PHASE ITEMS
Package State Update Phase 358/358
Image State Update Phase 2/2
Finally, we need to ensure that the ‘xauth’ file is included in the current PATH (to ensure that the OS is able to find the location of this file by default). This is easily done by editing the .profile or .bash_profile settings for the PATH environment variable, as shown below:
PATH=$PATH:/usr/X11/bin
export PATH
And we can start the VNCserver process as shown below (remember the password that is specified in order to connect to this VNCserver process later on)
root@sc2:~# vncserver :1
You will require a password to access your desktops.
Password: Verify:
New ‘sc2:1 (root)’ desktop is sc2:1
Creating default startup script /root/.vnc/xstartup
Starting applications specified in /root/.vnc/xstartup
Log file is /root/.vnc/sc2:1.log
And now we are able to connect remotely via a VNC viewer/client software (such as the freeware TightVNC viewer) to our Oracle Solaris 11 machine, and run whatever graphical management tools/installers we would like over the network